Did you know that 70% of organizations feel insider attacks have become more frequent? Whether the attacks are by malicious employees trying to steal information or external hackers exploiting vulnerabilities, endpoint security software can protect your company’s valuable resources. Implementing a protective solution entails you have a firm grasp of critical endpoint security requirements.
Get our Endpoint Security Software Requirements Template
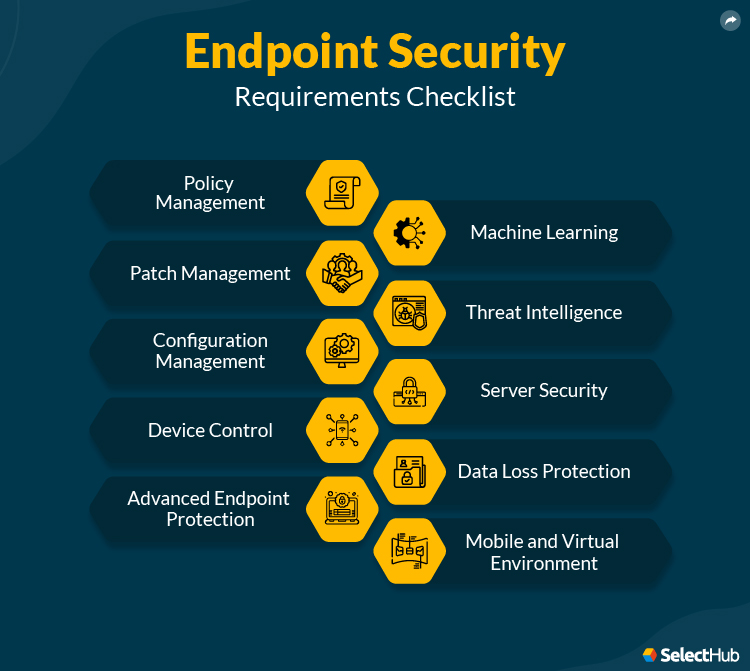
Endpoint security provides your company with the means to protect all endpoint devices, such as PCs, workstations, tablets, phones and servers. But in order to get the right functionality from your endpoint protection system, you’ll need to come up with a list of requirements.
As luck would have it, we’ve created an endpoint security requirements checklist to help you decide what features your company needs from its endpoint security software integration. Use it with our customizable template to create your list of requirements.
This article will:
- Specify key endpoint protection features that you should explore.
- Help you ask some questions as a starting point for your research.
- Understand the next steps to consider before investing in software.
Table of Contents
- Key Features and Requirements
- Policy Management
- Patch Management
- Configuration Management
- Device Control
- Advanced Endpoint Protection
- Machine Learning
- Threat Intelligence
- Server Security
- Data Loss Protection
- Mobile and Virtual Environment
- Security Management
- IoT Security
- Endpoint Detection and Response
- System Performance and User Productivity
- Importance of Requirements Gathering
- Needs Analysis
- Advanced Security Tools
- Next Steps
Choosing the right software during the vendor selection process can be confusing because of the wide variety of options that offer different tools and features. Our comprehensive checklist can help you avoid such distractions and assist in selecting the best endpoint security software solution.
Key Features and Requirements
Endpoint protection solutions offer much more than simple frontline defenses. To help you research and evaluate vendors, we’ve created a list of endpoint security requirements and key features you must be aware of:
1. Policy Management
Policy management is really just a fancy term for what kind of rules you can set for users and devices. Companies can use policy management tools to decide who gets access to certain data and what tasks they have to perform to get it. You can set up policies custom to the user and the device.
Manage device security with Microsoft’s endpoint security policies. Source
You can also set up policy override protocols to allow higher-ups access to data wherever needed. Additionally, override procedures include alerts and audit trails, making it easy to trace unauthorized access.
- Device-Based Policies
- User-Based Policies
- Override Policies
2. Patch Management
Patch management helps repair security vulnerabilities in a timely manner. Many cyber attacks target weak points in a system for which you’ve already created a patch. But it takes a certain level of vigilance to ensure each device in a company is up to date, especially when using end-of-life operating systems or with several employees working remotely.
Patching vulnerabilities has become even more difficult due to the coronavirus pandemic, with employee-owned devices dispersing across large distances and accessing corporate networks.
Get automated patch management capabilities with Endpoint Central. Source
Patch management automates the collection and delivery of patches company-wide. Some systems can create a convenient list of devices that need patching and allow users to schedule and deploy patches remotely.
It also uses machine learning and analysis to determine patch priority. If one device needs multiple patches, your endpoint security solution should be able to determine which patch to address first.
- OS and Applications
- Asset Management and Discovery
- Remote Devices
- Deployment Architecture
- Scheduling Updates
3. Configuration Management
These tools provide a centralized control panel to manage all your other endpoint security requirements and protection features. System administrators use configuration management to edit and establish policies, receive alerts, view audit trails and detect when users attempt an override. This allows greater visibility into threats and helps administrators make exceptions when users need to access certain applications or information.
Customize your level of aggression when protecting your endpoint devices. Source
Conversely, system administrators can completely shut down processes when an unauthorized user attempts restricted activities. Furthermore, this is the space where users can perform or schedule mass updates outside of work hours. But users can install software or update endpoints individually as well.
- Defining and Managing Configuration
- Policy Editing
- Scalability
- Exception Management
- Application Control
- Automatic Client Updates
- Live Security Alerts
- Mass Updates
- Remote Software Installation and Updates
Get our Endpoint Security Software Requirements Template
4. Device Control
This feature allows users to inspect external devices connected to the endpoint, typically through USB. However, many systems also can monitor local disks, CD and DVD drives, Bluetooth connection, and cloud storage. Moreover, users can choose which devices to allow and which to block.
For instance, you may allow a USB-connected mouse but not a USB-connected hard drive. You can apply exceptions using product information such as serial numbers.
Gain complete device control with Endpoint Protector’s capabilities. Source
Additionally, device control supports encryption of any data that does make it onto an external device. Unauthorized parties won’t be able to access any of the stolen data without the encryption key. Further, device control can extend to offline endpoints or endpoints not connected to the company network. These systems will log all user activity offline while enforcing usual policies.
- Multiple Device Support
- USB Device Access Control and Monitoring
- Workstations
- Encryption Algorithms
- Offline Support and Forensics
5. Advanced Endpoint Protection
Even though the internal threat to corporations is large, it’s still an important endpoint security requirement to ward off outside attacks. Top endpoint security systems protect against known security threats and zero-day attacks. These systems can block attacks from email, social media, P2P applications (like Skype and Dropbox) and websites. It ensures the protection of your devices and employees where they use the internet the most.
Monitor internet activity to prevent insider attacks. Source
Endpoint solutions protect against viruses, rootkits, Spyware, Trojans, Worms and the like. Companies can utilize these systems to detect and automatically remove threats using heuristics and other advanced detection technologies.
- Blended Threats/Malware Protection
- Host-based Intrusion Prevention System (HIPS)/Behavioral Analytics
- HTTP/Malicious Traffic Detection (MTD)
- HTTPS Malware Detection
- Automated Malware and Threat Removal
- Web Filtering
- Potentially Unwanted Application (PUA) Blocking
- Email Filtering and Attachment Scanning
- Botnet Protection
- Exploit Blocker
- Social Media Protection
- Peer-To-Peer (P2P) Applications
6. Machine Learning
Increasingly automated and well-orchestrated cyber threats like viruses, malware, ransomware, trojans, bots, keyloggers, zero-day and other constantly growing cyberattacks make it difficult for security teams to manage them effectively. Vendors utilizing advanced technologies like AI and machine learning in modules like EDR and XDR can keep your security infrastructure aligned with the ever-changing threat landscape.
Detect malicious threats quickly with AI and ML integration. Source
Machine learning can analyze a remarkable amount of data to understand typical endpoints or user behavior. You can use this information to identify suspicious or malicious activities and, consequently, alert security staff or trigger automatic actions before threats get executed on your devices. It incorporates multi-factor authentication, analytics and file-system level permissions to prevent data loss and ensure overall security.
- Multi-Factor Authentication
- File-System Level Permissions
7. Threat Intelligence
Advanced security systems integrate with third-party vendors to harness the power of threat intelligence. Threat intelligence solutions gather raw data from multiple sources about existing or emerging modern-day threat actors. This data is analyzed and filtered to provide real-time updates, help generate proactive defense mechanisms and mitigate potential risks.
Get targeted intelligence with CrowdStrike. Source
- Real-Time Threat Updates
- Proactive Defense
Get our Endpoint Security Software Requirements Template
8. Server Security
When shopping for a new security solution based on a set of requirements, you’ll want to ensure all your endpoints are protected. Servers are especially sensitive endpoints, so choosing a system that can protect them just as well as a PC is important.
Make sure your system can block threats to collaboration servers, data storage servers, internet gateways and email servers. Some vendors apply existing features to protect your servers, while others use specialized tools for each server type.
Secure your websites with cloud-based endpoint security.
- Collaboration Servers
- File Servers
- Gateway Servers
- Encryption Algorithms
- Email Servers
9. Data Loss Protection
Data loss protection (DLP) includes tools that allow system administrators to manage the network and prevent data loss and leaks across all company endpoints. DLP works through encryption, customized rules, remote access and user authentication. Encryption tools prevent employees from sharing files through the internet via chat or email.
Further, if the system administrator detects a user attempting to share privileged information, the admin can remotely wipe the hard drive to prevent breaches.
Secure your files by extension to protect your most valuable documents. Source
- Endpoint Encryption
- DLP Configuration
- Remote DLP
- Secure Authentication
10. Mobile and Virtual Environment
80% of phishing attacks targeted mobile devices in 2023. Therefore, the way you need server protection from your endpoint software, your company also needs protection for mobile devices. Just like with a desktop, endpoint solutions allow restriction of application use. You can choose which apps a user will have access to and can monitor activity as well.
For further security customization, admins can set lock screen timers and password requirements and block camera usage. And in the case of stolen or lost property, an administrator can erase all data from the device.
This feature also supports virtualized environment security. Virtualized environments are a great way to maximize capability from existing hardware, but you must protect each virtual machine (VM). Endpoint security solutions protect your VMs even when they exist in the same physical equipment.
- Mobile Device Management
- Mobile Security
- Virtualized Environments
- Full Disk Encryption
Get our Endpoint Security Software Requirements Template
11. Security Management Options
On-premise and cloud-based security both have their pros and cons. But most top systems offer both management options, so this requirement won’t affect your software selection. However, it’s still good to look out for so you don’t find the system of your dreams just to learn that endpoint security vendors don’t offer it in the cloud or vice versa.
Cloud systems offer security management from any internet-connected device and can provide robust reports and real-time notifications. Cloud-based products also reduce the initial resources spent setting up the system. On-premise software isn’t necessarily more expensive long-term, but it does require more investment upfront.
It also gives companies more control and privacy, as they can host all the data in-house. However, this privacy benefits hackers as well. With an on-premise system, they can launch “practice” attacks on their own servers without anyone knowing what they are working on.
It’s much harder to find vulnerabilities in cloud-based products since they need constant connection to the vendor who can detect attacks.
- On-Premise
- Cloud-Based
- Hybrid
12. IoT Security
Companies and employees are embracing IoT trends worldwide to facilitate complex business processes, boost connectivity and promote digital transformation. The global IoT security market is expected to grow from $662.21 billion in 2023 to $3352.97 billion by 2030, registering a CAGR of 26.1%. The COVID-19 pandemic has accelerated this growth with a significant shift towards remote work and work-from-home environments.
Unfortunately, the growing influx of IoT-enabled devices and increased connectivity poses new IT challenges to enterprises. These unmonitored devices form a porous security perimeter, attracting medium to high-severity attacks. Security solutions incorporating whitelisting to block unauthorized IP addresses or software and continuous file monitoring to identify unusual behavior or changes can safeguard your IoT devices.
13. Endpoint Detection and Response
With the increasing sophistication of cyber threats, the endpoint security market has evolved to advanced security approaches like Endpoint Detection and Response (EDR). EDR tools continuously monitor endpoints to detect suspicious behavior, trigger automatic responses and collect data for threat analysis, preventing future attacks.
Symantec EDR displays alerts on connection failure. Source
- Continuous Monitoring and Data Collection
- Complete Visibility
- Automated Response
- Analysis and Threat Hunting
14. System Performance and User Productivity
Explore security products with a small footprint so you don’t overburden your system resources like CPU, RAM or disk storage. A lightweight solution can preserve bandwidth and processing speed without negatively impacting productivity during scanning processes. Also, look for a non-intrusive suite that does not degrade the user experience.
Interactive alerts provide a better user experience. Source
- Lightweight Agent
- Non-Intrusive
- User Productivity
Advanced Security Tools
Apart from providing frontline defenses, endpoint security systems also offer analytics capabilities. With the rapid growth of the threat landscape, next-generation platforms are integrating advanced features like XDR, EDR, MDR and UEM.
These solutions help IT security teams proactively hunt threats and analyze the extent of the damage. They also offer AI and ML-enabled advanced analytics reports to fix vulnerabilities and prevent future attacks.
Importance of Requirements Gathering
Requirements gathering is a core part of the decision-making process of any business. It helps companies clearly define their vision, schedule, cost and scope. Knowing what requirements are essential for your business allows you to make the right decisions in your software selection process.
Needs Analysis
Here are a few questions you need to ask yourself before creating the requirements list:
What objectives are you trying to accomplish?
Security breaches are increasing at an alarming rate, and traditional antivirus solutions provide minimal security benefits to organizations. As signature-based security tools, they don’t protect against unknown malware and create new vulnerabilities due to integration issues with modern operating systems.
These challenges can also occur with endpoint security requirements that don’t meet your individual use case. Therefore, you should carefully examine your security needs and required capabilities.
Does the vendor offer solutions specific to your industry?
Look for endpoint protection features that satisfy the expectations of your company’s industry. These industry-specific solutions are essential for meeting compliance mandates. You must consider the company’s future development and growth to discern how scalable your new system should be.
What’s your cybersecurity budget?
Cost is a significant factor to evaluate in your endpoint protection requirements. The prices of solutions vary significantly depending on the number of tools, technical assistance and implementation support offered by the products. After creating your endpoint security checklist, you can cut unwanted costs and make better decisions.
How many IT professionals does your company have?
Security systems require ongoing supervision, maintenance and manual updates. To achieve optimal security, you’ll need IT professionals and security operations centers (SOCs) to ensure optimal security. Consider the IT workforce your company already has or will require in the future, and then choose a solution accordingly.
Select the Right Software with the Free Lean Selection Book
Next Steps
Compiling your list of endpoint security requirements before selecting a system is vital. If you need more help getting started, take a look at our free requirements template.
After you’ve decided what features and other aspects of endpoint security software your business needs, it’s time to compare vendors. In addition to our customizable template, we offer a free comparison report detailing the top systems’ endpoint protection features and how they compare to each other.
Our analyst team scores each vendor based on how well they offer top requirements, like the ones listed above. Use the report along with your requirements to see which vendor can provide you with the perfect endpoint security solution for your business.
So, what will you be looking for in your next system? Let us know if you have any endpoint security requirements we didn’t list in the comments below!